How Hamas Spied On 100,000 Israeli Soldiers
I don’t enjoy complimenting sworn enemies, but kudos to them.
I’m particularly annoyed (I’m fucken livid) about the following story because I wrote the beginnings of this frikkin problem all the way back in 2008!
How this was left unaddressed all the way to 7 October 2023 needs to be investigated as part of a National Commission of Inquiry into Israel’s worst intelligence failure (kidding there’s not going to be a commission).
During the October 7 attack, Hamas squads managed to disable Israeli tanks in the Gaza envelope and render them inoperable. Terrorists activated a kill-switch that was supposed to be concealed, causing the temporary neutralization of the vehicles. For months, the army tried to understand how Hamas knew about this function, which was considered classified. Only at the beginning of 2024 was the answer discovered, after IDF forces located an underground compound known as “The Pentagon” in Gaza. This turned out to be the intelligence nerve center for the Jihadi group. Now the army has revealed some of what was learned there, and I’m seeing red.
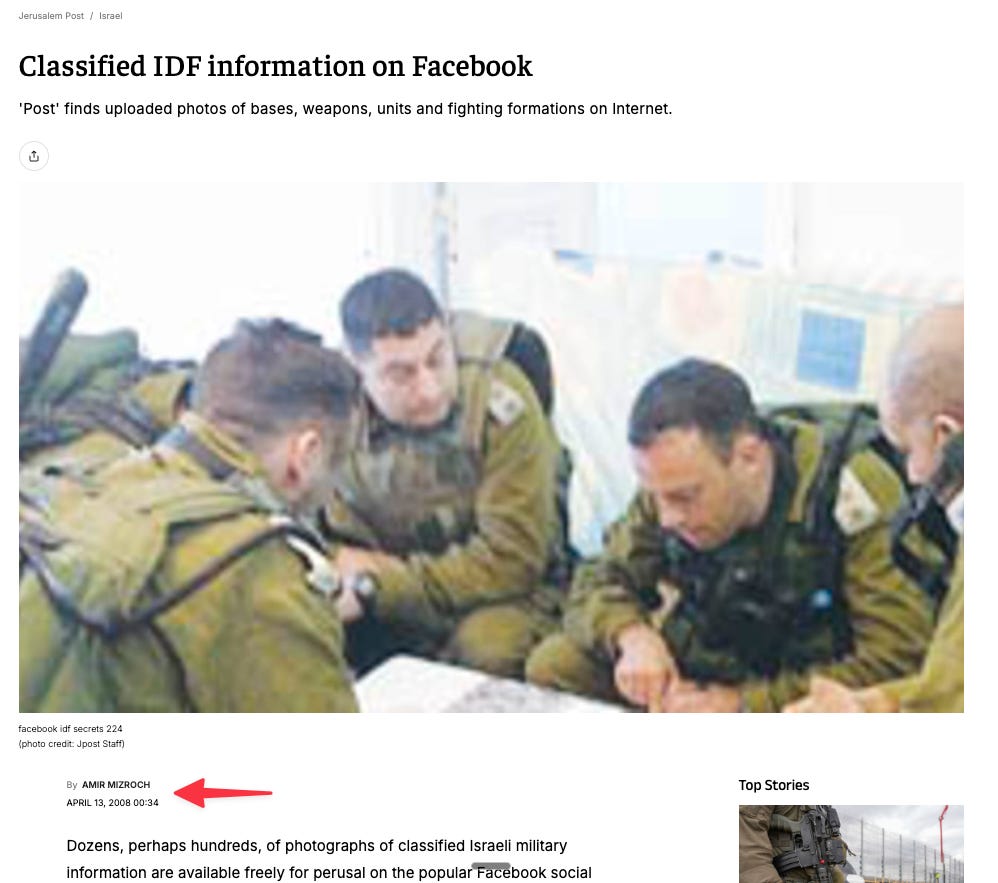
The IDF investigation published this weekend revealed the depth of Hamas’s intelligence collection apparatus. The tank kill-switch was just one example. For five years, Hamas tracked nearly 100,000 Israeli soldiers across social networks. Gaza’s rulers established a network of impersonator accounts that befriended soldiers and officers on Facebook and infiltrated WhatsApp groups mimicking IDF units, such as the “Egoz Recruits” group. They tracked combatants from initial recruitment through their progression to platoon and company command positions.
Hamas military intelligence cross-referenced this data to map the location of every company, every missile battery. They monitored each “classified” deployment in real-time—the moment soldiers complained about it in internal WhatsApp groups. They harvested photos and videos from bases to decode facility layouts, security camera positions, interior tank configurations, weapons systems. Training videos posted by soldiers at an armor training base. “Mundane” photos and clips from inside Merkavas. Instruction footage. Casual documentation that individually meant nothing. Then Hamas built full-scale Merkava Mark IV tank replicas and advanced simulator software to train what they called their “Tank Corps”.
Hamas had trained elite squads as IDF tank operators. Not just disable-and-destroy. Capture and operate. The plan: seize Merkava tanks during the October 7 assault and drive them into Gaza, to use against IDF forces. The capture-and-extraction component failed, but the tanks couldn’t fight.
I don’t enjoy complimenting sworn enemies, but kudos to them. Respect to whoever architected this apparatus from nothing and managed it operationally for years. Unfortunate they’re on the opposing side. There’s much to reverse-engineer. But assuming that senior officer is now dispersed across half of Gaza, we must decode the strategic implications ourselves.
First implication: Hamas is not merely a “terror organization.” This operation required 2,500 Hamas personnel dedicated to intelligence collection and analysis—sustained over years with disciplined patience and institutional rigor. Mounting such an operation demands the resources of a small state, or at minimum a city-state. That’s what Hamas was, and regrettably appears to be reconstituting: an adversarial state entity positioned on the border, observing, listening, waiting for optimal strike windows. Hezbollah is no different.
Second implication: We regard WhatsApp as highly secure—with valid reason. End-to-end encryption renders message interception theoretically impossible during transmission. Except: humans constitute catastrophic vulnerabilities. Elementary social engineering breached the unit’s “perimeter of trust”, and soldiers freely shared intelligence believing themselves “among friends.”
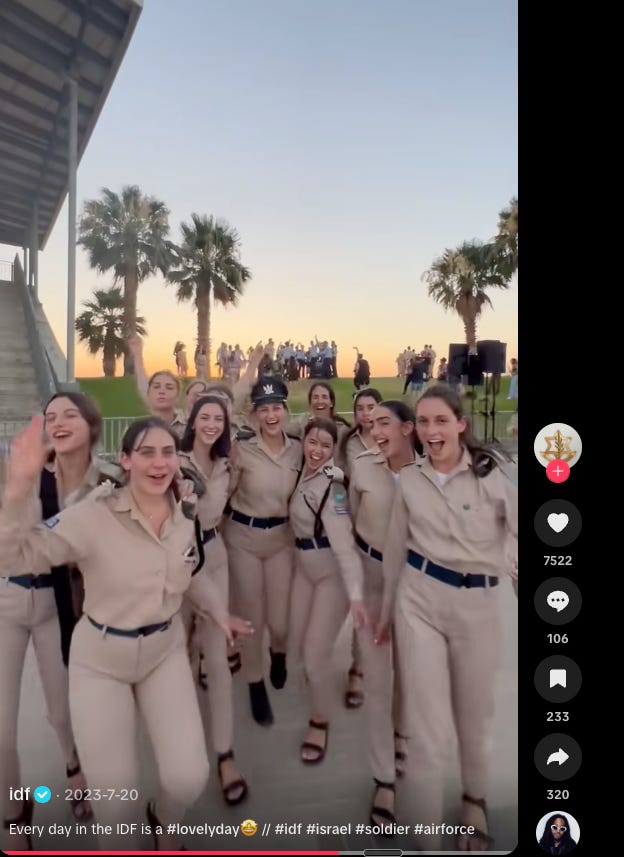
Perhaps most devastating: 100,000 IDF soldiers functioned as unwitting double agents—inadvertent Hamas collection assets. Every mundane Instagram story against a fence backdrop, every farewell photo near an armory, every TikTok barracks dance: each transmission fed the adversary incremental intelligence. Aggregated, these fragments rendered bases comprehensively compromised.
This exposes—once again— a fundamental flaw in prevailing information security doctrine. The IDF invests heavily in preventing classified document leaks. Meanwhile, massive amounts of intelligence hemorrhages through social networks while leadership throws up its hands with a “Kids these days…what ya gonna do?”.
But gather a steady stream of this content, rent a couple of servers in Malaysia, run pattern matching, geolocation, and other open-source analysis, and hey Presto, wipe out the entire Southern Division of the strongest country in the Middle East.
One officer acknowledged: “Hamas understood this base better than I did—and I served there for years.”
The remedy: Return to fundamentals. Zero information sharing on public networks. No TikTok content. No Facebook weapons photos from installations. Upload a video? Face court-martial.
Good luck enforcing that with a generation neurologically incapable of not documenting their existence.



No wonder governments are interested in hearing from Israeli militaries the new basics for urbane warefare. Good article. Thankyou
why is there a kill switch?